BitLocker Encryption Management Software

Centralized Management
Enhance BitLocker Encryption
Management
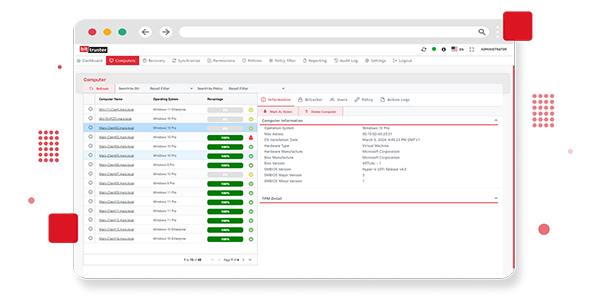
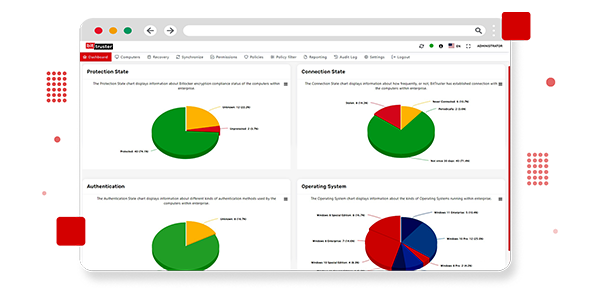
The BitTruster Centralized Management feature lets you manage all BitLocker encryption functionality from one convenient console. This integrated platform simplifies business tasks, and gives you a clear and comprehensive view of your encryption landscape. With real-time updates and centralized control, you can effectively manage encryption settings, monitor system status, and perform critical actions with ease. Increase your productivity with our advanced management tools and ensure consistent data security throughout your organization.
Compliance Reporting
Stay Compliant with Detailed
Reporting
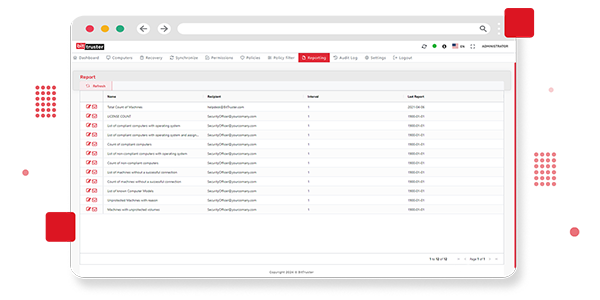
Ensure your organization meets regulatory requirements with BitTruster’s Compliance Reporting feature. Our platform provides detailed BitLocker reports and audit logs, enabling you to track encryption status, policy adherence, and system changes. These comprehensive reports facilitate thorough audits and help you demonstrate compliance with data protection standards. Stay informed and maintain regulatory compliance effortlessly with our robust reporting capabilities.
Policy Enforcement
Automate and Enforce BitLocker
Policies
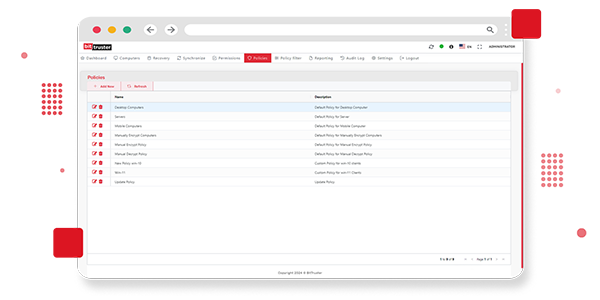
With BitTruster’s Policy Enforcement feature, you can automate the application and control of BitLocker regulations throughout your company. Define and enforce encryption requirements effectively, ensuring consistent data safety and reducing non-compliance risks. Streamline security operations by implementing and maintaining your security rules with precision. Our solution simplifies policy deployment, allowing you to focus on other crucial aspects of your IT infrastructure while ensuring robust data protection.
Secure Recovery
Protect Your Data with Reliable Key
Management
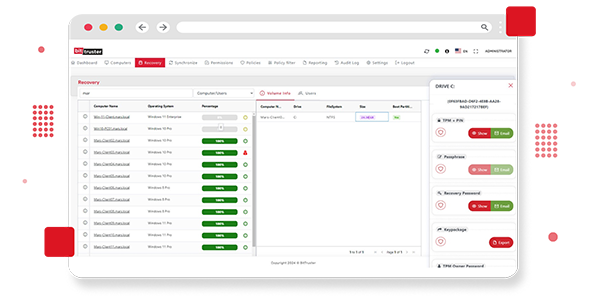
Protect your organization’s data with BitTruster’s Secure Recovery feature. Our platform offers reliable management of BitLocker recovery keys, ensuring that you can quickly and securely access encrypted data if needed. With robust key handling and recovery options, you can protect against data loss and maintain operational continuity. Trust BitTruster to provide the protection and support you need for effective data recovery.
Seamless Rollout
Deploy BitLocker Encryption
Smoothly
Get simple and efficient BitLocker encryption using BitTruster. Our Seamless Rollout feature simplifies the deployment process, reduces disruption and ensures consistent encryption coverage throughout your organization. Enhance your data security infrastructure with ease by leveraging our deployment solutions. Whether you’re using BitLocker for the first time or expanding its use, BitTruster makes it easy to configure, allowing you to secure your data more effectively and efficiently.
We Serve Key Global Customers With Our Premier Solutions And Expertise











